Tech-challenged federal prosecutors leak Steubenville hacker’s passwords, personal info.
Deric Lostutter, the Anonymous-affiliated hacktivist who helped expose a 2012 rape case against high school athletes in Steubenville, Ohio, is facing federal prosecution and a possible sentence of 16 years in prison for his alleged hacking. His case is scheduled to go to trial Nov. 8 in Lexington, Kentucky.
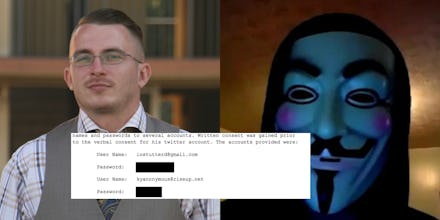
In a development that calls into question prosecutors' technical savvy, on Tuesday, Assistant U.S. Attorney Neeraj Gupta inadvertently published a trove of Lostutter's personal information — including his and his wife's Social Security numbers, his phone number, the login and passwords for his private email and chat accounts and his laptop and PC passwords — on PACER, a publicly accessible database of federal court documents.
"The government feels as though they can prosecute a case for cybercrime, but they can't properly redact a document," Tye Farley, a crisis manager working on Lostutter's case, said in an interview.
Lostutter's defense team first discovered the leak when detractors distributed the information on social media. Since 2013, Lostutter has been the target of harassment online, where his critics have claimed he doesn't deserve the notoriety for his role in exposing the Steubenville incident.
Through his lawyer, Lostutter has asked Judge Robert E. Wier to seal the documents. A hearing is scheduled for Wednesday afternoon to consider the matter.
A spokesman for the Office of U.S. Attorneys for the Eastern District of Kentucky acknowledged the error. "Our office has been attempting to seal that information," the representative said in an email.
The sensitive information was contained in an FBI report about a raid on Lostutter's home in June 2013. Prosecutors tried to redact sensitive portions of the document, placing black boxes over Lostutter's personal information and passwords. But simply opening the document in a PDF reader allows the user to remove those boxes. The information can also be retrieved by copying the text and pasting it into a word processor. The user who created the redactions in the object metadata is "NGupta," indicating that whoever redacted the document was using software registered to Assistant U.S. Attorney Neeraj Gupta, the leading prosecutor.
As of Wednesday afternoon, the information remains publicly available.
There's a dark humor in the redaction failure: Lostutter stands accused of accessing online accounts without authorization. By publishing his personal information and passwords, prosecutors have enabled Lostutter's harassers to commit this very crime.
"There's no small irony in that," Tor Ekeland, Lostutter's defense attorney, said.
Lostutter is being prosecuted under the Computer Fraud and Abuse Act, a law reviled by the tech community for being too broad in its scope and draconian in its sentencing guidelines. The CFAA is used as a catch-all that could apply to anyone using an online account that isn't their own; it could even be used to prosecute someone for sharing their Netflix password.
Both the judge and the defense have called into question the prosecution's choice to pursue charges against Lostutter in Kentucky three years after the alleged crime.
"If you consider the people who have it in for Deric and combine that with the fact that he can't monitor anything going on with his identity, it's unfortunate," Ekeland said. "Because the damage is done now."