Hackers used stolen NSA methods in massive, worldwide ransomware attack
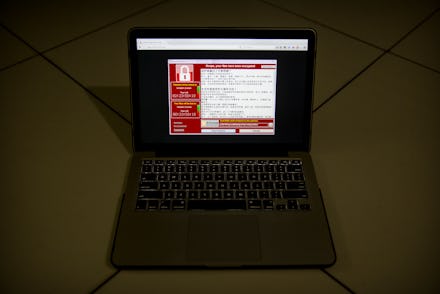
Security researchers said a massive ransomware attack now known to have hit over 150 countries and at least 100,000 organizations appears to have been designed using leaked National Security Agency data.
The malicious software, which spread over email and locked computer systems with threats they would be wiped unless users paid money to the hackers, is widely believed to exploit tools stolen from the NSA and distributed online, the New York Times reported.
Russian cybersecurity company Kapersky wrote the attack used an exploit method, "EternalBlue," originally developed by the NSA and released by a group calling itself the Shadowbrokers on April 14. The exploit allowed hackers to remotely seize control of many Microsoft Windows, and Kapersky wrote that although Microsoft posted a fix by one month later, many users had not updated their systems.
The ransomware started in Russia and quickly infected computer systems ranging from FedEx to the U.K.'s National Health Service, shutting down hospitals, and was only stopped by luck when a 22-year-old British cybersecurity researcher accidentally discovered a "kill switch" hidden in the code, according to the Guardian. Activating the kill switch turned off the ransomware worldwide, isolating the outbreak in Europe and Asia and likely preventing its widespread proliferation in the United States.
Though the ransomware component of the tool largely worked as intended without the use of exotic methods, Kapersky wrote, the use of the NSA exploit allowed the attack to spread much more quickly than it could have otherwise.
According to the Times, former intelligence operatives said the tools released by the Shadowbrokers are likely from the NSA's Tailored Access Operations division, which designs specialized cyberweapons to infiltrate computer networks around the globe. The NSA's practice of identifying security flaws in software, and then keeping those weaknesses secret so the NSA could continue to exploit them, led to widespread concern in the security community about what would happen if people outside the government were able to acquire that information — exactly what appears to have happened in this case.